Cybersecurity: Risk of insider threats is rising

After COVID-19 compressed years of digital transformation into a few months, digital and cloud investments continued to outpace cybersecurity spend despite a surge in new identities, new environments and new AI-fuelled attack methods that increased risk and burdened security teams.
The risk of insider threats is rising, with 74pc of organisations saying insider threats have become more frequent. Insider threats refer to cyberthreats that stem from an ‘insider’ in a company and usually entail sensitive data being leaked or stolen through employee access.
Workforce reductions and increasing workloads have a big impact on employees’ mental health and their ability to do their jobs effectively, as revealed by 59pc of UK senior cybersecurity professionals in CyberArk’s 2023 Identity Security Threat Landscape report. Businesses must understand the causes of the rise in insider threats and adapt to protect their critical assets. More specifically, controlling sensitive and privileged access to minimise the risk of data being unwittingly leaked is key. Identity security must be a priority.

Clarence Hinton, Chief Strategy Officer at CyberArk commented: “The results from our global survey of 2,300 security decision makers demonstrates the longtail effect of today’s cybersecurity decisions on future business outcomes, offering data-driven insights to help inform prioritization strategies and amplify security impact. We believe that by placing identity at the heart of a Zero Trust cybersecurity approach, following a risk-based strategy to secure critical assets and leaning on the expertise of trusted partners, organizations will be best positioned to weather the current storm, minimize risks and face the future with confidence. The question of who and what to trust is now at the forefront of preventing cyber debt compounding. Stakes are high and because of this we see customer-driven initiatives to consolidate trust, where organizations aim to focus operations with a smaller set of partners to build long term resilience.”

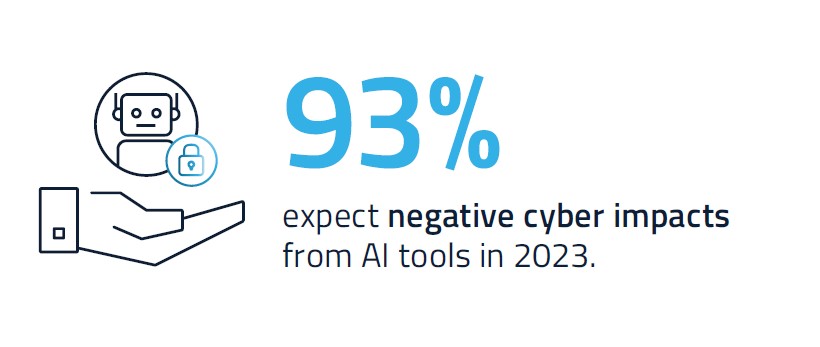
Often understaffed, under-resourced and charged with protecting a rapidly growing identity portfolio, security decision-makers cite growing challenges across six distinct areas of identity security risk:
- PEOPLE
74% of respondents are concerned about confidential information loss stemming from employees, ex-employees and third-party vendors. They point to third parties (partners, consultants and service providers) as the riskiest human identities that security teams have to deal with.
- WORKFORCE UPHEAVAL
68% of respondents say layoffs and higher levels of employee churn will create new security issues. For example, 58% report instances of exiting users saving sensitive or confidential work documents outside of policy. Every time an employee leaves, the IT team must remove access permissions from the various applications they used.
- MACHINE IDENTITIES
Due to increasing IT complexity, 62% of security teams operate with limited visibility across their environment. This makes it difficult to understand not only who is accessing sensitive data and assets but also what they are accessing.
- BUSINESS SYSTEMS
When considering the IT environments where unmanaged and unsecured access is most prevalent, 42% of respondents say business-critical applications top their list of at-risk systems. Yet more than half of all respondents admit that identities are unmanaged and unprotected in revenue-generating customer facing applications, enterprise resource planning (ERP), customer relationship management (CRM) and financial management software.
- SOFTWARE DEVELOPMENT
With a need for speed and flexibility, software developers are often given more access than required — especially in lean times when rapid innovation is key to survival. Perhaps security teams don’t have bandwidth to handle continuous access requests or developers are applying extra pressure. Regardless, 77% of respondents say developers have too many privileges — making these human identities highly attractive targets. Thirty-eight percent say the development realm is where unknown, unmanaged identities create the most risk.
- IDENTITY SECURITY TOOLSETS
Security professionals’ jobs are further complicated by a patchwork of heterogeneous tools from various vendors, creating identity security gaps in some areas and inefficient overlaps in others. Sixty-seven percent of respondents say they currently use tools from up to 40 different identity security vendors — underscoring a need for greater interoperability and vendor consolidation.
READ FULL REPORT HERE